E-commerce is unquestionably a key pillar of the world’s economy.
Case in point: The 2021 holiday shopping season saw consumers spend more than $1 trillion on gifts and other purchases. So, when such an important sector is vulnerable to fraud — especially the kind of fraud that impacts multiple parties at once — then it’s important to take notice.
Triangulation fraud is something that impacts multiple players and extends risk beyond the traditional paradigm. Below, Fraud and Financial Crime Expert PJ Rohall explores what triangulation fraud is; how merchants, acquirers and consumers can protect themselves; and what Featurespace is doing to prevent triangulation scams.
Table of contents
- What is Triangulation Fraud?
- How does Triangulation Fraud work?
- Who are the victims?
- How to avoid triangulation fraud?
- Outsmart triangulation fraudsters
What is Triangulation Fraud?
Triangulation fraud is when a customer makes a genuine purchase on a third-party marketplace, but the product they receive was fraudulently purchased from a different retailer’s website. This is a convenient scheme for cybercriminals, who take advantage of smaller merchants to make some quick cash.
Often, banking customers imagine fraud as something committed by a lone actor. That’s typically not the case with triangulation fraud. This is a relatively easy scam to pull off for an organization, but for individual fraudsters it might not be worth the effort because the scam is complicated, with several moving parts.
How does Triangulation Fraud work?
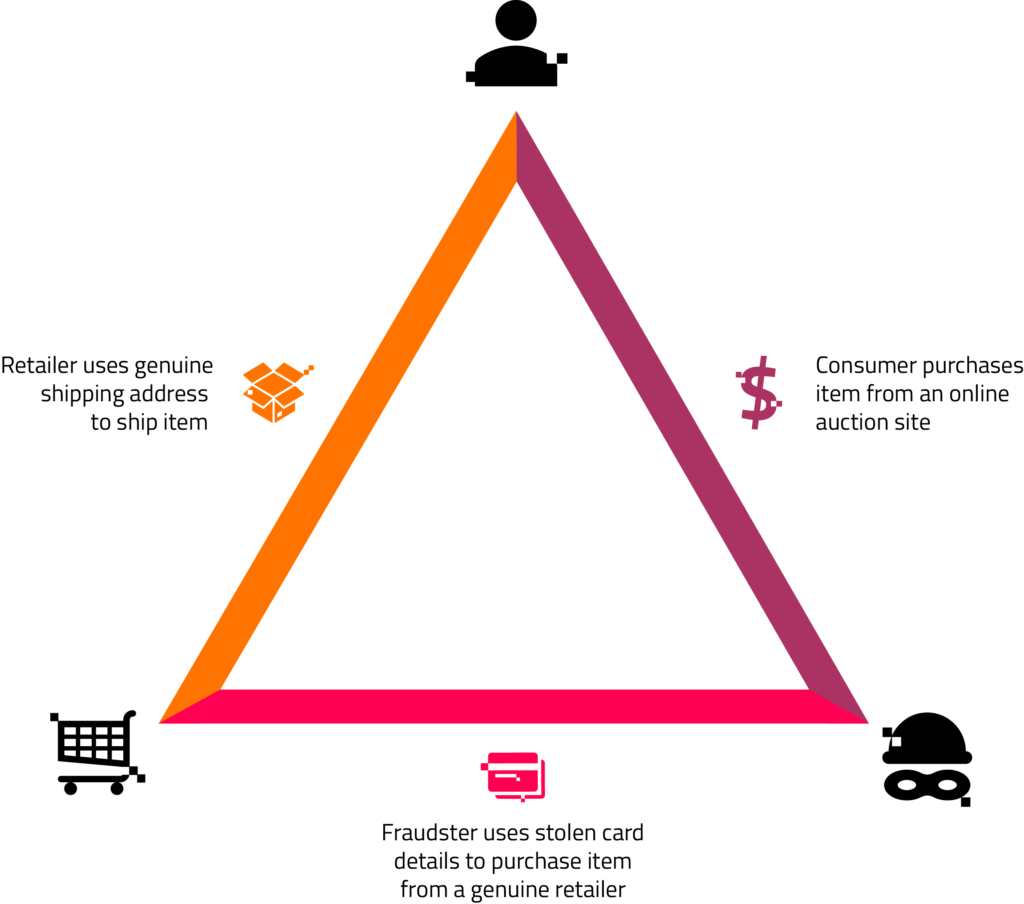
Attacks often follow a similar pattern:
- An unsuspecting customer makes a legitimate purchase on a third-party marketplace.
- The marketplace seller (the hidden fraudster) then places an order with a genuine retailer who has the product the customer wants.
- The fraudster uses stolen payment details to pay for the order but includes the genuine customer’s shipping information in the order, so the product is shipped to the customer.
- The owner of the stolen payment information disputes the charge with the genuine retailer who sold the product to the customer.
- The fraudster gets away with the original customer’s money, impacting a string of parties in the process.
Who are the victims of Triangulation Fraud?
Triangulation fraud affects several people:
The retailer
Unless they have appropriate security measures in place, the retailer is saddled with the chargeback. They are also out of the goods shipped. The negative impact goes beyond monetary losses, too: The retailer’s brand and the acquirer’s brand can be tarnished, as well as their relationships with the genuine customer and the genuine cardholder.
The genuine customer
When all is said and done, the genuine customer is now in possession of stolen merchandise, which will likely get taken away during the merchant investigation process. To top things off, the genuine customer’s shipping information is linked with the fraudulent transaction, and he/she may experience friction with future orders to that address.
The genuine cardholder
As with many fraud schemes, there is a true cardholder whose payment information is used to make the fraudulent purchase. While ultimately that person is financially reimbursed, the genuine cardholder may have gone days without access to their money.
The merchant acquirer
The acquirer is liable should the retailer not be able to satisfy the chargeback costs. Merchant fraud involves some especially complicated scams. If you would like to know more about merchant acquiring fraud prevention, have a look at what ARIC™ Risk Hub does to combat such scams.
The issuer
If the merchant leverages 3DS in their fraud prevention, the liability will sit with the issuer.
The introduction of PSD2 legislation has spurred wider adoption of 3DS 2.0 by merchants across Europe, with a corresponding shift in liability from merchant to issuer. Further, there is a breach of trust between the issuer and the genuine cardholder. If the cardholder feels their money isn’t safe in the issuer’s hands anymore, they could take their business elsewhere.
As e-commerce evolves, so does fraud
Traditionally, fraud may be thought of in terms of a criminal using stolen information to directly defraud the merchant. However, there is nothing traditional about the array of fraud happening in the e-commerce space.
With friendly fraud, the customer is the fraudster. With triangulation fraud, the person who ends up with the fraudulent goods is not the fraudster. Sometimes, the fraudster in triangulation fraud is a fraudulent website and not an individual selling on a marketplace.
E-commerce is the fastest-adapting channel for fraud. Further, the number of players and the amount of risk in e-commerce fraud are fluid, muddying the waters at every turn.
How to avoid triangulation fraud
There are some useful checks that can easily be implemented to combat triangulation scams.
Leveraging device ID, both in terms of reputation and velocity, is very helpful. A lot of times, these fraudulent players are a small group operating from the same device or set of devices. Whether single individual or separate storefront, strong intelligence here can nip the fraud ring in the bud.
In addition, comprehensive trend and link analysis will reveal common attributes in a lot of triangulation fraud. This is a bit more labor-intensive and reactive, but you can leverage historical data to map out and link common data points. This can then be fed back into your analytics.
More advanced fraud Modus Operandi call for advanced measures.
Leading organizations are using in-session control with behavioral biometrics to reveal anomalous user behavior in real time. User behaviors — including familiarity with the webpage, copying and pasting details, data input familiarity, and more — can reveal how a fraudster’s activity differs from a genuine user’s. This type of profiling can detect anomalous behavior in real-time and jump start a more proactive solution.
Adaptive Behavioral Analytics takes things a step further. It leverages machine learning and a variety of data inputs to build and understand the full behavioral profile. It begins with device ID intelligence and in-session behavior but does not stop there. Adaptive Behavioral Analytics ingests data across all channels, financial and non-financial, to develop granular behavior profiles and capture the full scope of a customer’s behavior.
The adaptive models enable fraud prevention to shift away from reactive and labor-intensive strategies. This is extremely beneficial when capturing complex fraud attacks and delivering top-notch KPI’s.
Outsmart triangulation fraudsters
While fraudsters’ Modus Operandi and the victims’ responses often seem convoluted and multifaceted, it all comes down to the same basic elements: human beings misleading other human beings for financial gain.
Fraudsters are simply shifting up and down the chain of risk, wearing different hats and launching different schemes. For potential victims, it’s critical to be vigilant, understand your role, understand the behavior and trends, and protect yourself accordingly.
Increasingly, merchant acquirers and payment facilitators are making innovative fraud solutions available to their merchants. Often, this means providing them a white-labelled product that can defend against more sophisticated fraud attacks through a multi-tenanted environment — offering a tailored experience to suit the merchants size and need.
As fraudsters continue to grow more sophisticated in their attacks, the ability to offer these services becomes a key competitive differentiator for the acquirer or facilitator.
Share

 by
by